A new report from cybersecurity company Netskope reveals details about attack campaigns abusing Microsoft Sway and CloudFlare Turnstile and leveraging QR codes to trick users into providing their Microsoft Office credentials to the phishing platform.
These campaigns have targeted victims in Asia and North America across multiple segments led by technology, manufacturing, and finance.
What is quishing?
QR codes are a convenient way to browse websites or access information without the need to enter any URL on a smartphone. But there is a risk in using QR codes: cybercriminals might abuse them to lead victims to malicious content.
This process, called “quishing,” involves redirecting victims to malicious websites or prompting them to download harmful content by scanning a QR code. Once on the site, cybercriminals work to steal your personal and financial information. The design of QR codes makes it impossible for the user to know where the code will direct them after scanning.
Thomas Damonneville, head of anti-phishing company StalkPhish, told TechRepublic that quishing “is a growing trend” that “is very easy to use and makes it harder to check if the content is legitimate.”
Quishing attacks via Microsoft Sway
In July 2024, Netskope Threat Labs discovered a 2000-fold increase in traffic to phishing pages via Microsoft Sway. The majority of the malicious pages used QR codes.
Microsoft Sway is an online app from Microsoft Office that comes free and enables users to easily create presentations or other web-based content. The app being free of charge makes it an attractive target for cybercriminals.
In the attack campaigns exposed by Netskope’s researcher Jan Michael Alcantara, victims are being targeted with Microsoft Sway pages that lead to phishing attempts for Microsoft Office credentials.
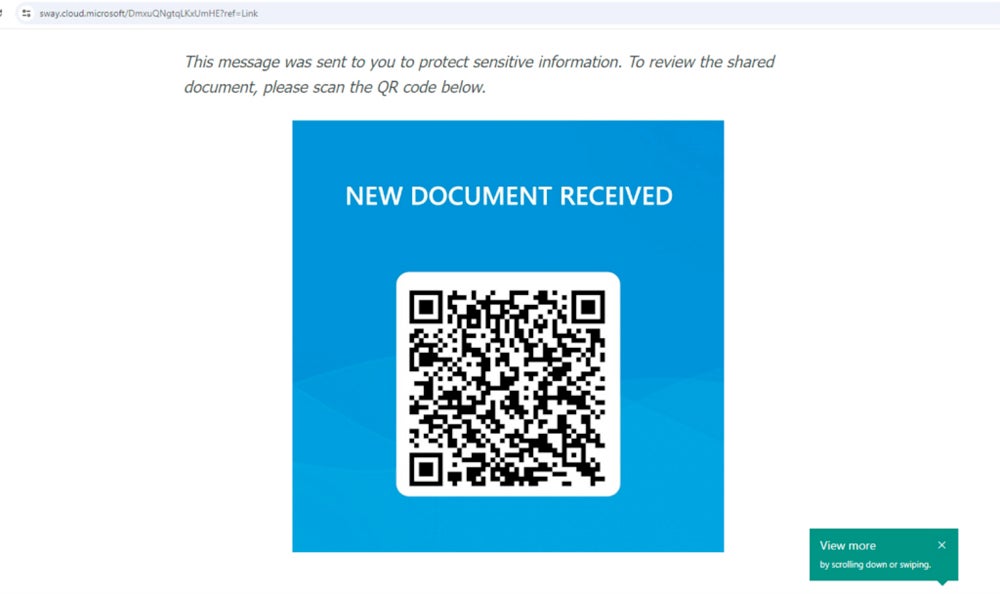
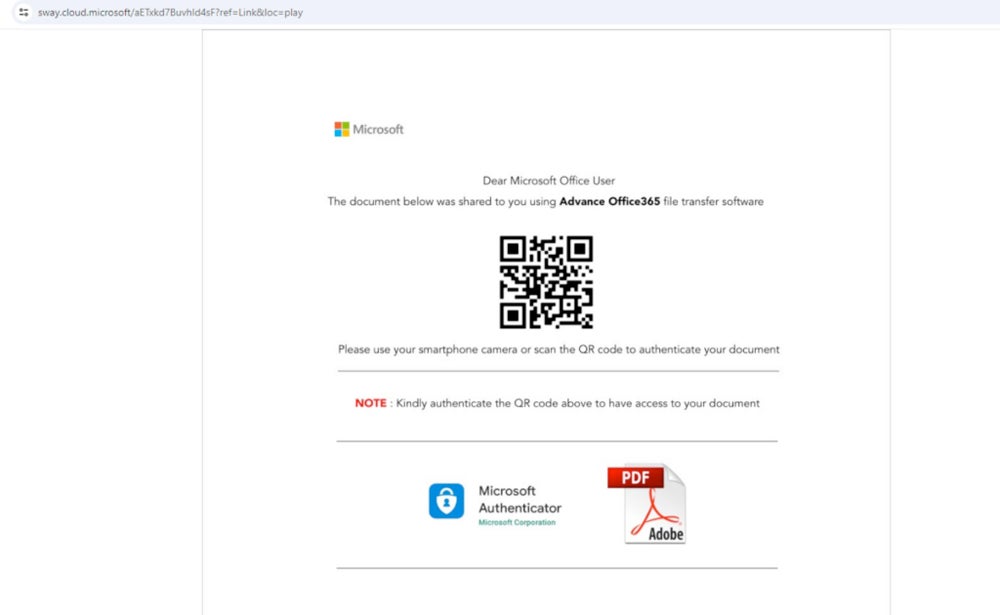
Netskope’s research does not mention how the fraudulent links were sent to victims. However, it is possible to spread those links via email, social networks, SMS, or instant messaging software.
The final payload looks similar to the legitimate Microsoft Office login page, as exposed in a May 2024 publication from the same researcher.
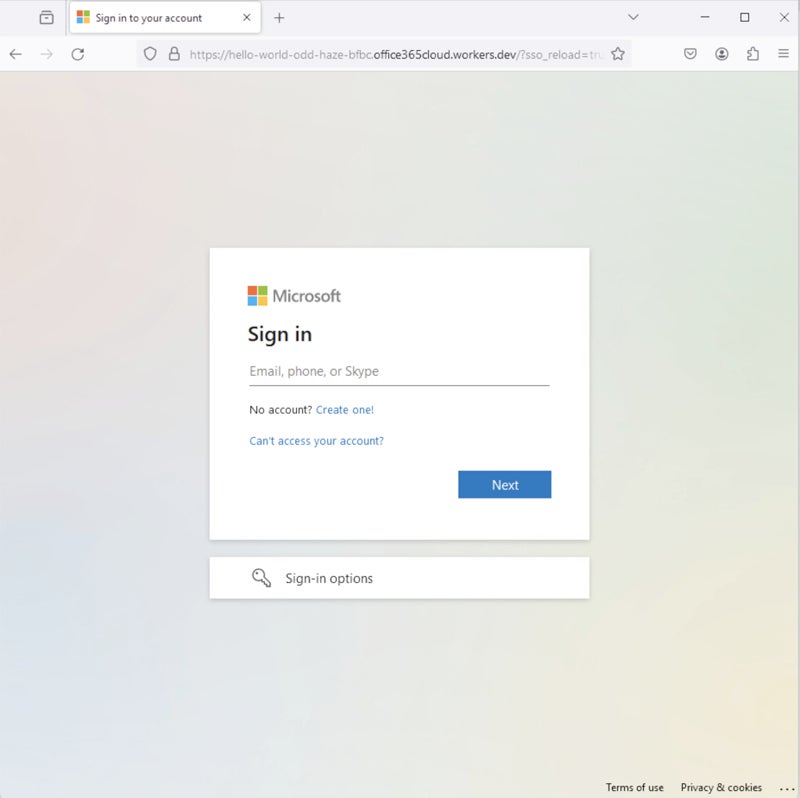
Stealthier attack using CloudFlare Turnstile
CloudFlare’s Turnstile is a free tool that replaces captchas, which have been exploited in reported attack campaigns. This legitimate service allows website owners to easily add the necessary Turnstile code to their content, enabling users to simply click on a verification code instead of solving a captcha.

From an attacker perspective, using this free tool is appealing because it requires users to click on a CloudFlare Turnstile before being redirected to the phishing page. This adds a layer of protection against detection for the attacker, as the final phishing payload is concealed from online URL scanners.
Attacker-in-the-middle phishing technique
Traditional phishing techniques typically collect credentials before displaying an error page or redirecting the user to the legitimate login page. This approach makes users believe they have entered incorrect credentials, likely leaving them unaware of the fraud.
The attacker-in-the-middle phishing technique is more discreet. The user’s credentials are collected and immediately used to log into the legitimate service. This method, also called transparent phishing, allows the user to be successfully logged after the fraudulent credential theft, making the attack less noticeable.
Malicious QR code detection difficulties
“Nobody can read a QR code with his own eyes,” Damonneville said. “You can only scan it with the appropriate device, a smartphone. Some links can be so long that you can’t check the whole link, if you check it … But who checks links?”
Text-only-based detections are also ineffective against QR codes as they are images. There is also no widespread standard for verifying the authenticity of a QR code. Security mechanisms such as digital signatures for QR codes are not commonly implemented, making it difficult to verify the source or integrity of the content.
How can you prevent a QR code from phishing?
Many QR code readers provide a preview of the URL, though, enabling users to see the URL before scanning it. Any suspicion on the URL should entice the user not to use the QR code. Additionally:
- QR codes leading to actions such as login or provide information should raise suspicion and should be carefully analyzed.
- Security solutions also might help, as they can detect phishing URLs. URLs should always be scanned by such a tool.
- Payments should not be done through QR code unless you’re confident that it is legitimate.
Microsoft Sway is not the only legitimate product that might be used by cybercriminals to host phishing pages.
“We regularly observe legitimate sites or applications being used to host quishing or phishing, including Github, Gitbooks or Google Docs, for example, on a daily basis,” Damonneville said. “Not to mention all the URL shorteners on the market, or free hosting sites, widely used to hide a URL easily.”
This once again enforces the idea that users’ awareness needs to be raised and employees need to be trained to distinguish a suspicious URL from a legitimate one.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.





