Cloud security is increasingly important, as more data moves to the cloud.
Cloud technology is not limited to data handling. We see companies taking the entire development process to the cloud. While it is an excellent strategy for scalability and flexibility, security remains a prime concern.
For example, you are a software development company based in Atlanta with remote developers scattered worldwide; how will you ensure access? The simplest way is to choose a cloud-based development service. However, the problem lies with the security of app users’ data and code libraries stored on the cloud.
On July 15, 2020, Twitter was hit by a cyberattack taking down more than 130 accounts, 45 unauthorized tweets, and 8 user-accounts were archived. As you can see in the tweet by Twitter support, they were still to verify the data breach’s exact cause by July 23rd.
The incident puts forth an example for enterprises to focus on cloud security. It is clear that cybersecurity is not something you can ignore. So, here are the four crucial factors that can help you create reliable cloud security for your business.
1. Cloud workload protection (CWP):
As you deploy a cloud security protocol, there is a need for central visibility. Cloud workload protection helps secure the workload across the cloud, especially with more app development distributing the workloads across clouds.
Let’s take an example of a company that wants to separate front-end and back-end software development. They may choose to have a multi-cloud strategy- one cloud provider for the front-end and another for the back-end.
So, the workload of the development process is distributed across clouds. You can secure cloud workloads by methods like micro-segmentation and bare-metal hypervisors.
Cloud Security: Micro-Segmentations
Micro-segmentations help with the protection of cloud workloads through network security. The approach helps to divide data centers into separate security segments at an individual workload level. Next, security architects can define separate controls for each control. Here, you can use network virtualization technology for micro-segmentation to define cloud security protocols. It helps with the prevention of malware attacks at the server level within the environment.
Cloud Security: Bare metal hypervisor
A bare-metal hypervisor helps to add an extra layer of protection to the cloud workload security. Virtualization software helps create and manage virtual machines by separating software elements from the hardware. Any bare-metal hypervisor can be installed between an operating system and hardware. It isolates the virtual machine(VM) under cyberattacks from other VMs, so those machines’ workload is not affected.
2. Integration Security:

Multi-cloud and hybrid strategies involve private cloud providers and public cloud platforms. When you integrate third-party APIs into cloud platforms for the exchange of data, security becomes paramount. APIs are a set of protocols that help data access, validation, and authentication between heterogeneous systems.
APIs are among the most vulnerable elements in cyberspace. To ensure proper API integration security, there are three types of methods you can use,
1. API Key Security:
An API key is a single token or a small physical device with information regarding the identification and authentication.
2. APPID/ APP Key:
It is a two token string security with a username and a password provided by the application. These IDs are specifically great for public clouds, where users are directly involved.
3. OpenID Connect (OIDC):
OIDC is an extra layer of security on top of Open Authorization(OAuth), allowing third-party services to access your resources without passwords.
3. Network Security:

Enterprises and companies with multi-cloud strategies will have a network of cloud servers and virtual machines. Apart from workload protection and authentication keys, data exchange is one of the most critical activities.
Let’s understand this with an example. Suppose you are a US-based enterprise looking to develop an application. Next, you find a development in Atlanta or Wisconsin to develop the app.
But, the front-end is outsourced to some UI/UX design agency from Barcelona. This agency uses an open-source platform for front-end development. Though it will help you reduce the cost substantially, but increase the threat of a cyberattack. Another issue is that you may have to store your codes in an open-source cloud service with potential cybersecurity risk.
So, what can you do to ensure complete network security across the enterprise?
A practical approach to network security is to employ an AI-based anomaly detection system. AI or Artificial Intelligence algorithms can help you identify anomalies in the network through different methods.
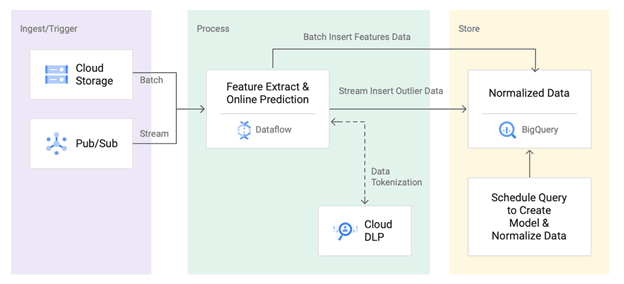
The conventional approach is signature-based anomaly detection, where network traffic is investigated against stored information on malicious anomalies. While modern clustering algorithms help analyze outliers through the distance of deviations from the network nodes.
4. Data Security:

In cloud security, all the transactions occur in terms of the most critical currency- “Data.” So, when it comes to data security, not just the companies or enterprises, government authorities worldwide stress on regulations. When the European Union’s top court shelved privacy shield on data transfers across EU-US regions, data regulations became more potent in European countries.
So, what can one do to ensure data security?
Apart from the standard, authentications, and data protection policies, identifying data objects can help secure the information. A standard application may include different data objects like core data with user database in the cloud or transitional data in the exchange between user’s devices and cloud services.
Data objects can be related to,
- PII(Personally Identifiable Information)
- Service audit data
- Service Level Agreement (SLA)
- Service profile information
- Temporary runtime data
Identifying the data objects allows you to place the right security measures in place. Another critical aspect is understanding the type of security agreements you may need from a cloud service provider. These are,
- Data confidentiality assurance
- Data integrity protection
- Guarantee of data availability
- Secure data access
- HIPAA(Health Insurance Portability and Accountability Act) & GDPR( General Data Protection Regulation) compliance
- Service audition agreement
Cloud Security Summary and Conclusion:
As the data resources become smarter with the Internet of Things(IoT) and other innovative devices, the complexity of securing them increases. With multi-cloud strategies, transitional data need real-time security and anomaly detection.
While Artificial Intelligence and Machine Learning algorithms help detect malicious attacks for cloud services, data classification is also quintessential to process. Here, we have discussed four critical parts of cloud security to help you create a secure data environment. Understanding these factors will enable you to have better cloud security strategies in place.




