These phishing emails promise compensation, test results, and other lures about the coronavirus to trick unsuspecting users, says Armorblox.
Image: iStock/OrnRin
Phishing campaigns often take advantage of events in the news as a way to hook potential victims, and that’s been especially true with COVID-19. Throughout this year, cybercriminals have exploited every aspect of the virus to capitalize on the fear, anxiety, and curiosity people naturally have felt about this deadly outbreak. A new report from cybersecurity firm Armorblox looks at four types of coronavirus-related phishing campaigns that appeared this year and suggests ways to defend against them.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
Scammers sniffed an opportunity with COVID-19 early in the year, prompting them to incorporate the pandemic into their phishing attacks. By the middle of April, Google’s Threat Analysis Group was detecting 18 million coronavirus-themed malware and phishing emails per day.
With 2020 almost over, such email attacks continue merrily on. Some are poorly designed and unconvincing, but many are expertly created and harder to distinguish from legitimate messages.
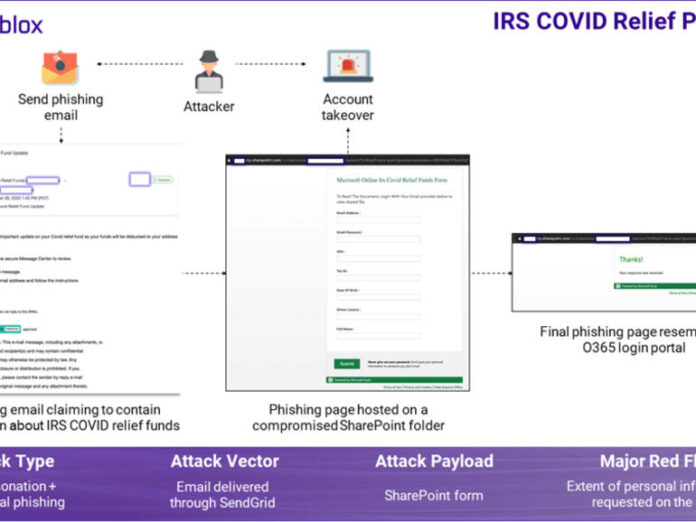
IRS COVID relief phishing
In this campaign, an email claimed to offer a document about IRS COVID relief funds with a link to this alleged document. Clicking the link would bring you to a SharePoint form to fill out. The form asked not just for your email account credentials but for data such as Social Security numbers, driver license numbers, and tax numbers, all of which the attackers would then capture.

Phishing email disguised as information about IRS COVID relief funds.
Image: Armorblox
This campaign used a variety of social engineering tactics to great effect. The subject of “IRS Covid Relief Fund Update” and the sender name of “IRS Covid Relief Funds” were both specific and design to elicit quick responses from recipients. Referencing an authority like the IRS also aims to prompt an immediate action. The phishing link pointed to a compromised but legitimate SharePoint page to evade the usual security protection that blocks malicious domains.
IMF COVID compensation scam
In this one, the phishing email claimed that the recipient was due COVID compensation from the International Money Fund (IMF). To get this compensation, the user was asked to reply to the email to provide further details, which would eventually be appropriated by the attacker.

Email scam disguised as COVID compensation news from the IMF.
Image: Armorblox
By not including an actual link to a phishing page, this email sneaks past any security filters that block suspicious links. The email also includes an entire conversation thread from an IMF director claiming that 125 beneficiaries had been shortlisted for IMF COVID compensation, a way to make the scam seem legitimate. The email title of “Re: IMF Compensation” and a reference number are also designed to lend legitimacy to the message.
COVID test results scam
Here, the email spoofed an automated message from a doctor’s office promising the recipient’s COVID test results. Clicking the link for the results tries to install a malware-infected RAR file on the system.

Email scam disguised as COVID test results from the doctor’s office.
Image: Armorblox
Using “Doctors Support” as the sender name, mentioning a nurse’s name, and offering COVID-19 test results are all designed to make the email seem legitimate. The message itself includes a password/PIN to access the attachment with the test results, giving the user a false sense of security.
SharePoint impersonation
In this scam, the email impersonated an automated message from SharePoint claiming to offer a file about COVID-19 requirements. Clicking the link for the file would take victims to a deceptive site hosted on AWS.

Email scam disguised as COVID test results from the doctor’s office.
Image: Armorblox
The sender name of “Sharepoint Online” and the email template mimic the information typically seen in automated emails from legitimate cloud applications. The subject of the email uses the recipient’s first name followed by “COVID 19 Requirements” in an attempt to create fear and anxiety. The message itself carries a footnote asserting that the link will work only for the email recipient, a key way to lull people into a false sense of security.
To protect your organization and your users from these types of phishing scams, Armorblox offers the following guidelines:
- Follow 2FA and password management best practices. Deploy two-factor authentication (2FA) on all possible business and personal accounts. Use a password manager to store your account passwords. Don’t repeat passwords across accounts or use generic passwords such as your birth date or obvious ones such as “password123” or “YourName123,” etc.
- Subject sensitive emails to rigorous eye tests. Engage with emails related to COVID in a circumspect and rational manner. Subject the email to an eye test that includes inspecting the sender name, sender email address, language within the email, and any logical inconsistencies within the email.
- Create your own lines of authentication. Try to replicate 2FA, even if in a loose sense, for COVID-related email that expects an action from you. For example, did your doctor just email you test results in an attachment? Call or text the doctor and confirm that they sent the email.
- Augment native email threat detection with additional controls To augment existing email security capabilities (e.g. Exchange Online Protection for Office 365 or the Advanced Protection Program for G Suite), invest in technologies that take a materially different approach to threat detection. Rather than searching through static lists and blocking known bad domains, these technologies should learn from custom organizational data and be able to stop socially engineered threats like payroll fraud, impersonation, and COVID-based email scams.