A match made in Heaven or a recipe for Hell? This article attempts to outline a future game plan that we can plot based on past trends and events
Have you ever wondered why Cybersecurity are not rebranding in this new era of business? Or has it already been repositioned? And as with all rebranding exercise, is the repositioning done with a purpose? With the coming of a new digital and sustainable future, one may find that even with the rebranding, it does not fully represent the purpose, value and vision that our industry may have and represent!
This is not the first time that our industry finds ourselves at the crossroads of time. As far back 30 to 40 years ago, cybersecurity was not in existence yet, but a sub-domain of the industry was starting to take shape. Known as EDP auditing where EDP stands for Electronic Data Processing in mainframe days, the need came from a need to manage operational risks from accounting and internal auditing perspective, especially those punch cards for batch processing can be quite unforgiving and hard to verify at that point in time, as one can only verify the end-results of the computation manually while the checks on the punch cards where mostly for transposition errors and the such. The EDP Auditor was the prototype of our profession then.
Subsequently as we fast forward into the 80s, with the proliferation of personal computers, we also saw a plethora of new threats such as computer viruses that infected the bios to the first worm (aptly named Morris) that sees the evolution of EDP auditors into two career path, one that followed the original trajectory of EDP auditors but instead of EDP, the focus is now on Information Technology (IT), whereas the new job type is organized under the bigger umbrella of IT or just information security professionals. Probably this is where this new profession and the original started two distinct paths of evolution where information security professionals developed further sub-job types. This is probably the golden age of information security and the first rebranding exercise of our industry!
Further down the road with the introduction of the Internet and the dawn of a new millennium, the focus extended further to the Internet. While it is not at the level that we are talking about, the meeting of worlds in the Metaverse, but with the introduction of the Internet there was still a massive shift towards defining the greater eco-system of how to secure the Internet, or the data that were utilizing the Internet. Arguments were frequent on the definition of end-to-end. Does it terminate at the software stack layer? Or does it end at the physical layer? And software delivery framework at that time were myriad, anyone remembers Sun One versus .Net framework? But at the heart of this discussion, was the evolution of the term information security or IT security, or for that matter, Internet security and network security, which are woefully wrongly used interchangeably even though they were not exactly identical.
As such, this brought in a new era and a new terminology that is still used today – cybersecurity, which at its most simple state means security of the cyberspace, as defined under ISO/IEC 27032 Guidelines for Cybersecurity first published in 2012. The diagram below depicts the core fundamental definition, boundaries and relationships between the different domains and nomenclature of its time, a long overdue clarity finally existed that attempt to demystify the roles and responsibilities of the various roles that exist in the market leveraging on these domains to attempt to scope it out clearly.
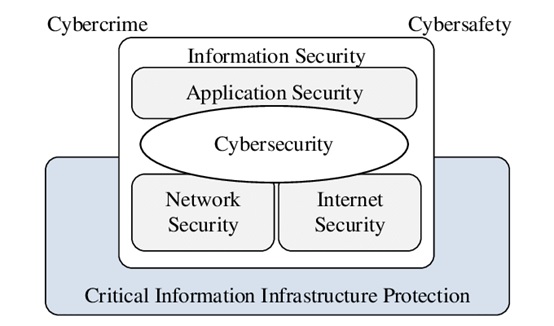
Unfortunately, while the term cybersecurity and its definition, including the domain and areas of responsibilities were now finally accepted as a global standard, however this does not help to move the industry forward as the industry was so fragmented that no new terminology, concept or trends were sufficiently to unify the industry. Notwithstanding that the term cybersecurity has a baggage of national security that divided the viewpoints and perspectives of many experts from different countries working on ISO/IEC 27032.
Fortunately, the God of Computing has a way of figuring out these things. A 0.5 version improved version of the “new era” brought the dawn of cybersecurity into the mainstream as IT became an utility and for the first time, we were not talking about justification for IT and security because of the concept of utility where IT is embedded into the business process and cybersecurity is embedded into IT. Yes, we are talking about Cloud Computing. Cloud is a game changer, and it totally changes the perspective of cybersecurity, and cybersecurity is no longer playing second fiddle to compliance but a critical feature that comes with the service itself. That is how powerful the concept of utility is, and cybersecurity was quick to reposition itself and rebrand itself as one cybersecurity unicorns after another were born in the era of the cloud, and we saw some down beaten IT security brands riding the wave and reinvent themselves as protectors of the cloud and rebadge themselves as cloud security companies.
So maybe we are now at a new crossroad again. Metaverse is prophesized to be the next big leap. While the opportunities promised are bountiful, but equally is the risk, as the attack surface and threat landscape are multifold in terms of magnitude and difficulty compared to today. But this is also the promised land for cybersecurity professionals. Because of rapid digital transformation due to the Covid-19 pandemic, we are seeing that more and more assets of companies are increasingly existing in the form and shape of digital compared to traditional, and to some extent for some organizations the digital assets outweighs the traditional assets. On the other hand, after a prolonged period of working from home, being confined in the brick and mortar of an office is no longer attractive, and the pandemic proved beyond doubt that you don’t have to come to the office to work. This changes the attack surface as well as threat landscape as organizations now have a boundless software defined perimeter that they are working with to defend their digital assets as the crown jewels that defined their very existence.
These trends catapulted the Chief Information Security Officer (CISO) into the limelight as the protector of these crown jewels. No longer hiding in the shadows of the back office or data centre and covering behind the tall and powerful figure of the Chief Information Officer (CIO), the CISO can stand on himself in the executive management team and a regular fixture on the Board because the risk register that the Board owned, now are talking about the risks brought about by the digital assets that the CISO is protecting today!Having said that, by no means that the CISO is rebranding themselves as ambassadors of trust or the soothsayer and influencer on social media. To be able to hold on themselves, to be credible, the CISO still need to retain their technical skills sets because eventually the role of the CISO is a technical leader and not a business leader. It has to be clear that business owns the risk, but the CISO owns the risk controls! The future of cybersecurity must be built on the basics to address future challenges! Be that as it may, the signs are on the wall – we are now entering
Golden age of the CISOs. And with the coming of the Metaverse, does this signal the start of a new bull run (on operational risks which will be synonymous with cybersecurity risks when worlds meet)?



