IoT devices are becoming integral elements of federal information systems, which is why NIST has released for public review draft guidance on defining federal IoT cybersecurity requirements, including supporting non-technical requirements. These four new documents expand the range of guidance for IoT cybersecurity, with the goal of ensuring IoT devices are integrated into the security and privacy controls of federal information systems.
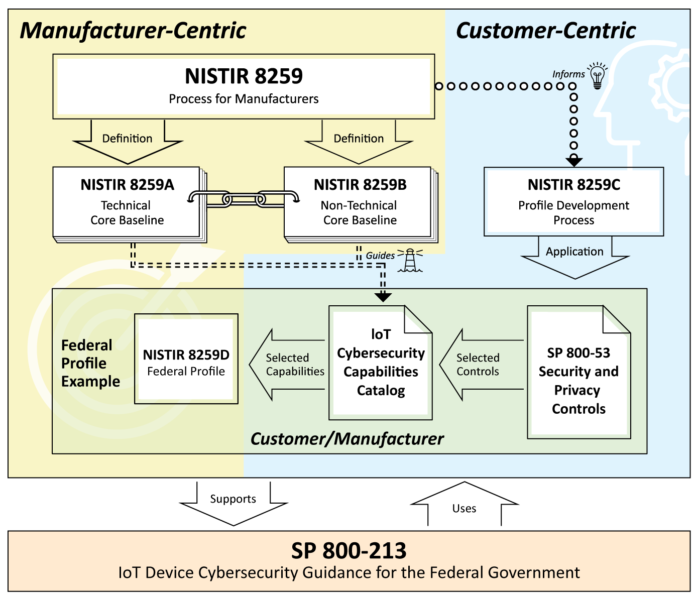
This figure illustrates the relationships among the documents.
The new documents are:
We’ve also created an updated version of our IoT catalog reflecting NIST and community input on these individual capabilities. These four documents build on the first two documents in NISTIR 8259 series, NISTIR 8259, Foundational Cybersecurity Activities for IoT Device Manufacturers, and NISTIR 8259A, IoT Device Cybersecurity Capability Core Baseline. They provide more complete guidance and specify a profile of our IoT cybersecurity requirements catalog for federal use cases, roughly aligned with the FISMA low-impact baseline.
Overall guidance for federal agencies seeking to integrate IoT devices into their systems and infrastructures is provided in SP 800-213. The SP has background and recommendations to help federal agencies consider how an IoT device they plan to acquire can integrate into a federal information system. IoT devices and their support for security controls are presented in the context of organizational and system risk management. The SP provides guidance on considering system security from the device perspective. This allows for the identification of device cybersecurity requirements — the abilities and actions a federal agency will expect from an IoT device and its manufacturer and/or third parties, respectively.
The NISTIR 8259 series provides the tools to implement SP 800-213’s guidance to develop specific requirements. Let’s walk through this family of documents and discuss how they are connected:
- NISTIRs 8259A and 8259B are a complementary pair, providing balance in our treatment of technical and non-technical requirements, and giving more comprehensive guidance for manufacturers executing the six activities called out in NISTIR 8259. While NISTIR 8259A provides the device cybersecurity core baseline,NISTIR 8259B details additional, non-technical supporting activities typically needed from manufacturers and/or associated third parties. This non-technical baseline collects and makes explicit supporting capabilities like documentation, training, customer feedback, etc.
- NISTIR 8259C describes a process, usable by any organization, that starts with the core baselines provided in NISTIR 8259A and 8259B and explains how to integrate those baselines with organization- or application-specific requirements (e.g., industry standards, regulatory guidance) to develop an IoT cybersecurity profile suitable for specific IoT device customers or applications. The process in NISTIR 8259C guides organizations to create a more detailed set of capabilities responding to the concerns of a specific sector, based on some authoritative source such as a standard or other guidance, and could be used by organizations seeking to procure IoT technology or by manufacturers looking to match their products to customer requirements. This method was used to create the profile meeting the requirements of the federal information system low baseline that’s defined in NIST SP 800-53B.
- NISTIR 8259D shows the results of applying the NISTIR 8259C process in a federal government customer space, where the requirements of the FISMA process and the SP 800-53 security and privacy controls catalog are the essential guidance. NISTIR 8259D provides a device-centric, cybersecurity-oriented profile of the core baselines, calibrated against the FISMA low baseline as an example of the criteria for minimal securability for federal use cases.
Organizations with needs that aren’t addressed by the Federal Profile contained in NISTIR 8259D should begin by applying the guidance in SP 800-213 to clearly define their security requirements and then execute the process described in NISTIR 8259C to develop an IoT cybersecurity requirements profile that fits their needs.
We look forward to the community’s feedback on these drafts as we work to provide IoT cybersecurity guidance that aids both the vendor community and the customer community in taking advantage of the benefits that IoT devices can bring while thoughtfully and effectively responding to the associated risks.