If you’ve purchased a FEITIAN FIDO2 device and can’t seem to get it working with Linux, Jack Wallen shows you how.
There are quite a lot of security devices available for users and admins to work with. Many of these devices offer the ability to save credentials such that only with that device present, can you log in to an account. That’s fundamentally how FIDO2 works, and there are plenty of companies that make such devices.
One company is FEITIAN.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
I was sent a few of their devices to review. I informed the company that my OS of choice is Linux and was assured that the products worked with the open source platform. According to the company’s website, it was just a matter of installing the BioPass Manager to configure the hardware key.
Unfortunately, that is not the case. After a bit of work and some help from the FEITIAN developers, I was able to get one of the products–the K26 FEITIAN BioPass FIDO2 Biometric Fingerprint USB-C Security Key.
I want to show you how to get this FIDO2-certified biometric key connected to Linux, so you can gain that added layer of security while using the open source operating system.
How to create a udev rule
This was the problem. Nowhere in the FEITIAN documentation does it mention having to create a udev rule, which enables the system to identify devices based on their properties, like vendor ID and device ID. Unfortunately, without that rule in place, the device cannot be recognized by Linux. So, what do you do? You create the udev rule. Here’s how.
Log in to your Linux system and create a rule file with the following:
sudo nano /usr/lib/udev/rules.d/70-u2f.rules
In the new file, paste the following:
# this udev file should be used with udev 188 and newer
ACTION!="add|change", GOTO="u2f_end"
# Feitian ePass FIDO, BioPass FIDO2, KeyID U2F
KERNEL=="hidraw*", SUBSYSTEM=="hidraw", ATTRS{idVendor}=="096e", ATTRS{idProduct}=="0850|0852|0853|0854|0856|0858|085a|085b|085d|085f|0862|0864|0865|0866|0867", TAG+="uaccess", GROUP="plugdev", MODE="0660"
LABEL="u2f_end"
Save and close the file. Once the file is saved, reload the rules with the command:
sudo udevadm control --reload-rules
At this point, the device should be recognized by the system.
How to download and run the BioPassFIDO2 manager
Now we need to download and run the BioPassFIDO2 manager tool. Download the file and unpack it with the command:
tar xvzf BioPassFIDO2-Manager-Linux-20200702.tar.gz
Once the file is unpacked, rename it with the command:
mv BioPassFIDO2-Manager-Linux-20200702 biopass
Launch the manager with the command:
sudo biopass/x86_64/BioPassFIDO2
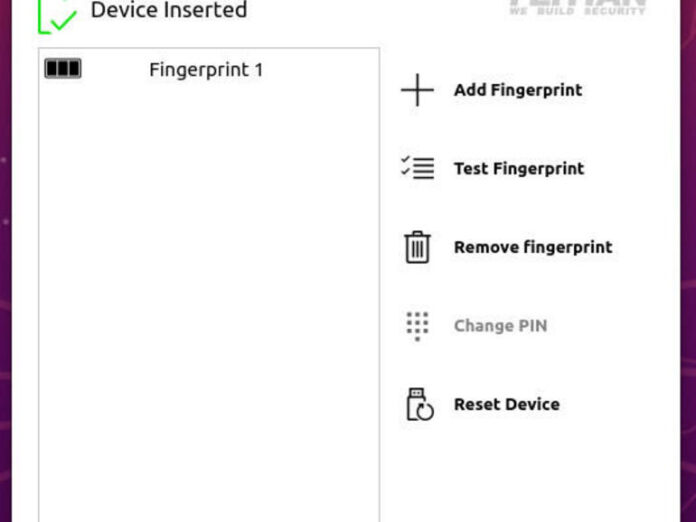
When the manager opens, your device should now be recognized (Figure A). Click Add Fingerprint and walk through the wizard.
Figure A

The FIDO2 device is now visible to Linux.
Once you’ve registered your fingerprint, you’re ready to start using it with sites that support FIDO2 authentication.
It’s a shame getting such a device working with Linux requires users to jump through hoops they don’t have to on other platforms. Fortunately, it’s a rare occasion that you have to manually create udev rules for hardware, but when you do, it can be a real hassle. Maybe someday, udev rules will be a bit more automatic for devices similar to this. Until then, you’ll be manually creating udev rules so those products can be recognized by the Linux operating system.