A new report for cybersecurity firm WithSecure suggests that most companies are investing in security solutions that are tactical and reactive, but not in line with strategic aims of an organization.
A new report by cybersecurity firm WithSecure, based on a survey of more than 400 global cybersecurity and IT decision-makers conducted by Forrester Consulting, suggests that many organizations are reactive in their approach to defending against threats, and piecemeal when it comes to cybersecurity investments.
The result? Security goals become detached from business goals, resulting in organizations investing in defenses against threats that aren’t relevant to their business or goals.
Outcome-based security versus reactive security
According to Forrester, an outcome-based security supports business goals rather than merely reacting to perceived vulnerabilities. It enables business leaders to simplify cybersecurity by “Cultivating only those capabilities that measurably deliver their desired outcomes as opposed to traditional threat, activity-based, or ROI-based methods,” said WithSecure’s report.
The report said a more holistic approach to cybersecurity should strive for outcomes related to risk management, customer experience, resilience, and visibility of the threat surface and risks. The outcomes should also pertain to skills, resources and response speed and agility (Figure A).
Figure A
Paul Brucciani, cybersecurity adviser and head of product marketing for solutions at WithSecure, said that the concept of outcome-based cybersecurity constitutes both a way to make cybersecurity executions align with business goals, and to reduce clutter and redundancy of security solutions and tactics. This is a Marie Kondo-esque effort to throw objects on the floor and discard those layers of control that don’t strategically support business goals.
SEE: Businesses whose goals include more clouds should expect rain.
“Outcome based security is a way to make decisions about what you need to protect and how. But it’s a discipline: it’s very easy to buy and implement a new tool, much more difficult to switch off legacy systems. To turn things off [that aren’t useful],” Brucciani said.
Even though 83% of respondents to the survey said they were interested in, planning to adopt, or expanding their adoption of outcome-based security solutions and services, 60% said their organizations are reactive, not proactive; they respond to individual cybersecurity problems as they arise.
One-fifth of companies align cybersecurity with business priorities
The study, which aimed to understand organizational cybersecurity priorities and business goals, found:
- Only 20% of respondents said their organization has complete alignment between cybersecurity priorities and business outcomes.
- 75% of respondents said cyber-risk management is receiving increased attention from the board of their organizations.
- 60% of firms are willing to spend 6% or more of their operational profit to achieve the benefits they see in adopting an outcome-based approach for cybersecurity investments.
- 50% of firms struggle to measure cybersecurity value and have trouble articulating the contribution of security to business outcomes.
‘Market of lemons’ paradigm complicates security investments
Cybersecurity budgets are rising, but could the sheer size and scope of the cybersecurity service market be driving IT buyers to allocate budgets haphazardly?
SEE: In this Q&A, an IT expert and consultant talks about how to prioritize security in budgets.
Brucciani said this is probably the case, as the current market for cybersecurity Software as a Service itself constitutes a “market for lemons,” a term coined by economist George Akerlof to describe a circumstance in which the market is peppered by good and bad products and the buyer is hobbled by an inability to discern which is which.
“Cybersecurity is a massive business; depending on how you define the market there are 10,000 cybersecurity companies in the world which creates a noisy marketplace, and many of those companies are venture capital backed, so their job is to get to market as fast as possible. As a consequence it creates a market that is difficult to navigate, with the added challenge of measuring quality: Buyers have no way of assessing the quality of what they are being sold,” Brucciani said.
What businesses seek from cybersecurity tools and services
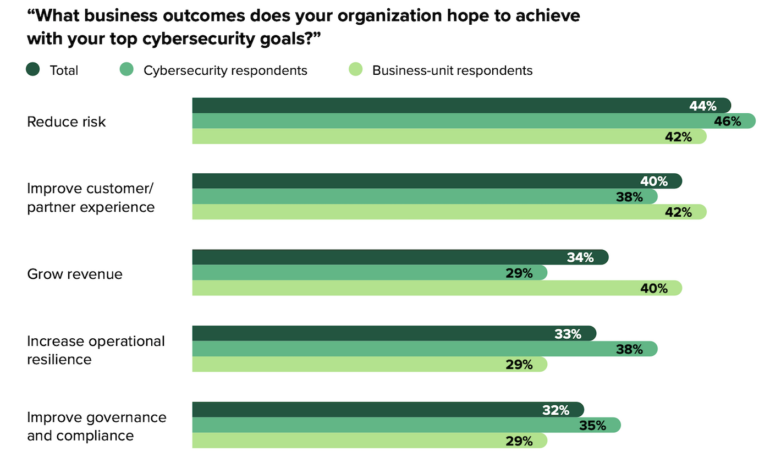
Survey respondents cited some of the biggest security challenges: visibility into cyber risks, finding the required skills and resources, and responding quickly and effectively (Figure B).
Figure B
Outcomes that respondents said they sought from cybersecurity efforts include:
- 44% of those polled want to reduce risk.
- 40% want security to improve customer experience.
- 34% want security to support revenue growth.
- 33% want to increase operational resilience.
- 32% want security to be aimed at governance and compliance.
Getting meaningful metrics tying security to business outcomes is another challenge
The executives polled by Forrester listed challenges to extracting useful metrics that tie security priorities to business outcomes:
- 37% expressed difficulties in measuring cybersecurity value.
- 36% said they could not capture consistent and meaningful data.
- 28% found challenges in overcoming a paradox: investment in effective security results in fewer opportunities to demonstrate value.
- 23% encountered challenges in translating cybersecurity metrics into something meaningful to the board.
Additionally, 42% said they had an insufficient understanding of current and target-state maturity against which security value should be assessed. Brucciani explained that target state, in a security context, is an expression of an enterprise’s security goals and depends on such factors as:
- Impact of a cyber security attack on the enterprise.
- Risk tolerance — the impact an enterprise can absorb and function.
- Willingness to take security risks.
- Security that regulators and clients expect.
“Generally businesses want a higher level of security than they have at present,” said Brucciani. “The question is, how much security is enough? Their cyber risk strategy — if it is coherent — will be driven by these factors.” He added that NIST offers a useful framework to support security decision-making.
How to build business outcomes into security
The study included recommendations on how to bring cybersecurity investments into strategic alignment with business goals:
- Business outcomes should be agreed on with stakeholders and mapped to your security investments, threat model, and security controls.
- Security outcomes should include business benefits (e.g. risk-based authentication in e-commerce improves CX by eliminating extra steps and friction from low-risk transactions).
- Security priorities should correlate to business outcomes, avoiding unnecessary investments in security that business outcomes don’t require.
- Procurement and legal teams should be prepared for outcome-based security purchasing.





